Releases Notes
Version 2.0.3
DownloadWhat's new
- Starting from Up2Dep version 2.0.0 we introduce checks for crypto API misuse in library versions. If a third party library happens to misuse a cryptographic API in their code, and your code re-use such code from the library, Up2Dep provides you a warning in form of error in your build.gradle file. Details on the libraries (versions) with cryptographic APIs are listed here.
- You can provide us feedback any time with the option "provide feedback on this check". This will greatly help us in improving Up2Dep
How does it work
We leverage CogniCrypt to analyze for cryptographic API misuse in third party libraries. All found missuses are stored in our database, and for API usages of such library (versions) inside your Android code will be examined against such misuses.
Examples
1. Up2Dep checks your dependencies and warns you against using outdated dep
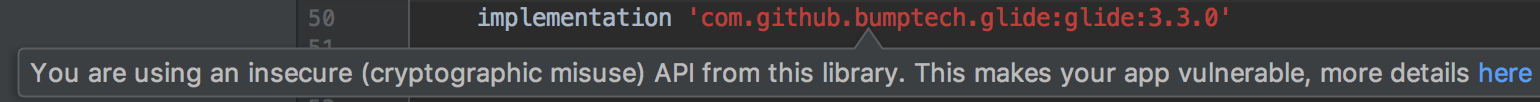
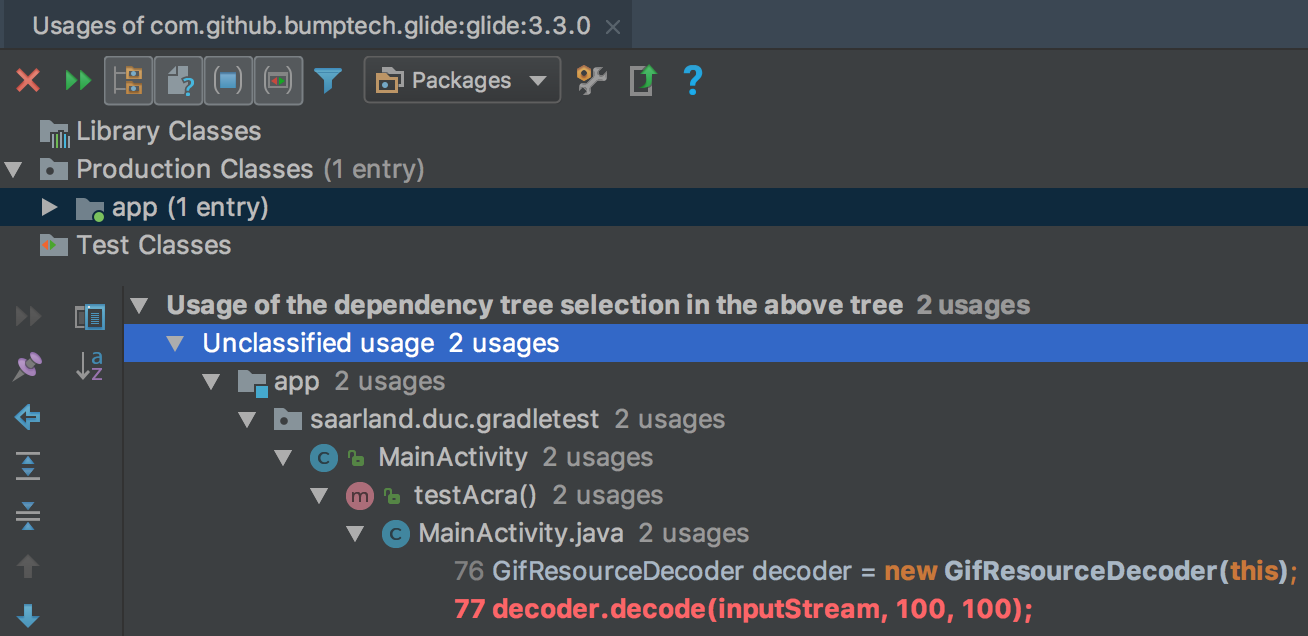
2. You can navigate to the usage of the insecure API that misuses cryptographic API. In this example the method: GifResourceDecoder.decode(InputStream source, int width, int height) uses SHA1 algorithm for MessageDiget which is considered insecure.
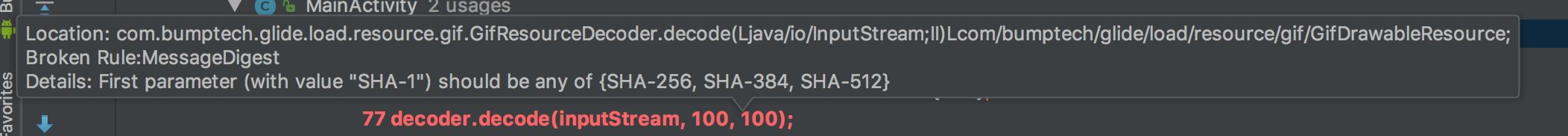
3. You can hover the mouse over the insecure API (in red) to get more information regarding the crypto misuse of such API.
Previous versions
16.01.2019
Version 2.0.2 is now available with bug fixes due to API changes in Android Studio 3.3, you can download it here or go to Usage to see how it works, more info about new features here.
15.01.2019
Version 2.0.1 is now available that is compatible with Android Studio 3.3, you can download it here or go to Usage to see how it works, more info about new features here.
14.01.2019
Version 2.0.0 is now available with Insecure API usages inspection, you can download it here or go to Usage to see how it works, more info about new features here.
27.09.2018
Version 1.0.1 is now available with support for Android 3.2.
30.08.2018
Version 1.0.0 is now available with performance improved; Kotlin language support; more libraries (now 1,521 libraries in total).
16.07.2018
Version 0.1.0 is now available on Android Studio plugin's repository. Up2Dep now includes vulnerable (insecure) library versions check. Furthermore, this version includes additionally 349 Android libraries (2877 versions) into the existing database.
29.06.2018
Version 0.0.2 is now available on Android Studio plugin's repository.
28.06.2018
We have fixed a performance bug which duplicates the local sqlite file hence incurs unneccessary local space.
We have updated Up2Dep with version 0.0.2 to JetBrains plugin's repository. Please wait for 1 or 2 days until it is available before trying out. Thanks to Martin for the bug report.